🔐 SOC Automation & AI‑Driven Threats Shape 2026 Landscape 🌐

Good day – Here is your daily Cybersecurity & AI Threat Intelligence roundup for January 25, 2026.
Today's headlines
- Real‑time blocklists dramatically cut alert fatigue for SOCs.
- GreyNoise early‑warning system improves CVE prioritization.
- KONNI harnesses AI to auto‑generate PowerShell backdoors.
- AI‑crafted malware fuels a large‑scale phishing campaign.
- Publicly available hacking tools continue to empower diverse threat actors.
1️⃣ Real‑time Blocklists Cut Alert Noise

Key Points:
- Fully configurable, real‑time blocklists block malicious IPs instantly.
- Reduces low‑priority and false‑positive alerts from internet scanners.
- Enables SOC analysts to focus on high‑impact incidents.
- Integrates with SIEM, SOAR, and TIP platforms.
Description:
GreyNoise’s latest blog outlines how its real‑time blocklist technology allows organizations to automatically filter out noisy traffic and block malicious IP addresses, streamlining alert handling and improving overall SOC efficiency.
Why It Matters:
By cutting down on unnecessary alerts, security teams can allocate resources to genuine threats, shortening response times and lowering operational costs while maintaining stronger defensive postures.
2️⃣ Early‑Warning CVE Alerts Boost Patch Prioritization
Key Points:
- Traffic spikes trigger early warnings of emerging CVEs.
- Provides visibility into active exploitation trends.
- Helps organizations assess risk severity quickly.
- Supports smarter patch management decisions.
Description:
GreyNoise introduces an early‑warning feature that detects unusual traffic patterns indicating new vulnerability disclosures, giving enterprises a head start on assessing and mitigating emerging threats before widespread exploitation.
Why It Matters:
Early awareness of actively exploited vulnerabilities enables faster patch deployment, reducing the window of opportunity for attackers and limiting potential breach impact.
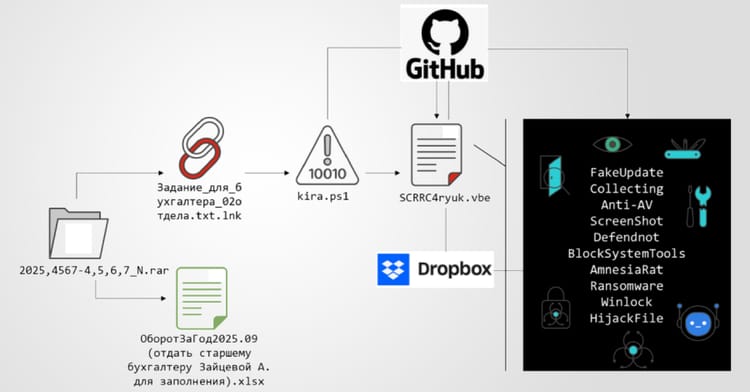
3️⃣ AI‑Generated PowerShell Backdoors Target Developers

Key Points:
- North‑Korea‑aligned actor KONNI uses AI to craft PowerShell scripts.
- Backdoors are tailored to evade static and behavior‑based defenses.
- Campaign specifically lures developers through malicious repositories.
- Demonstrates automated malware creation at scale.
Description:
Check Point researchers report that the threat group KONNI is leveraging generative AI to automatically produce PowerShell backdoors, distributing them via phishing emails and compromised developer tools to infiltrate target environments.
Why It Matters:
The automation of malware generation lowers the barrier for sophisticated attacks, forcing defenders to adopt AI‑aware detection methods and to harden development pipelines against supply‑chain compromises.
4️⃣ Phishing Campaign Leverages AI‑Crafted Malware
Key Points:
- Massive phishing operation distributes AI‑generated payloads.
- Emails spoof trusted developer communication channels.
- Malware encrypts files and exfiltrates source code.
- Rapidly adapts signatures to bypass traditional AV.
Description:
The same KONNI campaign extends to a broad phishing initiative that uses AI‑generated malicious attachments to compromise victims’ systems, aiming to steal intellectual property and install ransomware capabilities.
Why It Matters:
Combining AI‑crafted malware with phishing increases success rates and complicates detection, highlighting the need for advanced email security and behavioral analytics.
5️⃣ Publicly Available Tools Fuel Global Incidents
Key Points:
- Open‑source hacking tools are used by nation‑states, cybercriminals, and hobbyists.
- Incidents span health, finance, government, and defense sectors.
- Widespread tool access challenges attribution and response.
- Encourages coordinated monitoring and mitigation strategies.
Description:
CISA’s advisory highlights the growing prevalence of freely available penetration‑testing and exploitation tools in cyber incidents worldwide, emphasizing their impact across critical infrastructure.
Why It Matters:
The democratization of offensive capabilities expands the threat surface, requiring organizations to bolster detection of known tool signatures and adopt proactive threat‑hunting practices.
6️⃣ Compromised Asset Detection Shields Cloud Workloads
Key Points:
- Instant alerts when assets contact malicious IPs.
- Improves visibility of compromised cloud instances.
- Enables rapid isolation and remediation.
- Integrates with cloud security posture management tools.
Description:
GreyNoise’s compromised asset detection feature notifies organizations the moment a cloud workload communicates with a known malicious address, allowing quick containment actions to protect sensitive data.
Why It Matters:
Early detection of compromised assets prevents lateral movement and data exfiltration in cloud environments, safeguarding privacy and compliance obligations.
Stay vigilant and keep your defenses AI‑ready.