AI‑generated PowerShell backdoors rise 🔥 | GreyNoise filters cyber‑noise 🌐 | CISA warns on public tools 📢

Hello, here is your Daily Cybersecurity & AI Threat Intelligence roundup for Jan 25, 2026.
Today's headlines
- GreyNoise blog explains how real‑time blocklists cut through internet scanner noise.
- North Korea‑linked group KONNI uses AI to auto‑generate PowerShell backdoors targeting developers.
- CISA alerts that publicly available hacking tools are being leveraged across critical sectors.
- GreyNoise reports a surge in CVE exploitation spikes, prompting early‑warning alerts.
- Check Point releases analysis of a new vulnerability dubbed “The Next WannaCry”.
- Check Point unveils AI‑driven enhancements to its Threat Intelligence platform.
🔴 1️⃣ GreyNoise: Filtering Noise in (Cyber)Space

Key Points:
- Real‑time blocklists configurable for SMBs and enterprises.
- Reduces low‑priority alerts from mass internet scanners.
- Integrates with SIEM, SOAR, TIP, and firewalls.
- Provides early warning on CVE disclosure spikes.
Description:
GreyNoise released a detailed blog describing its platform’s ability to filter noisy, low‑value traffic by delivering fully configurable blocklists that can be fed directly into security tooling, helping SOCs focus on genuine threats while automating the suppression of benign internet background noise.
Why It Matters:
By cutting down false positives, organizations can allocate analyst time to higher‑impact incidents, improve response times, and lower operational costs, ultimately strengthening the overall security posture against real attackers.
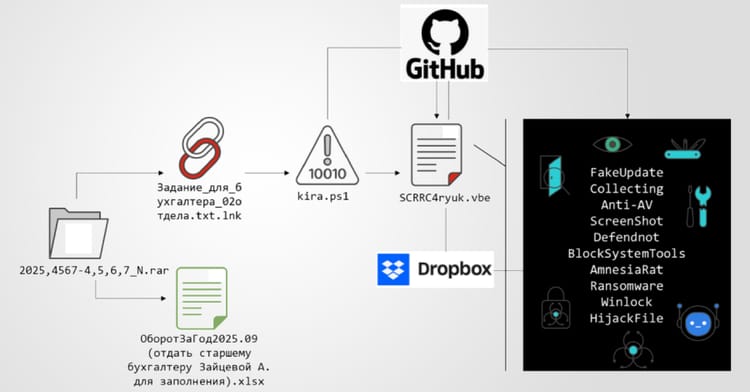
🟢 2️⃣ KONNI adopts AI to generate PowerShell backdoors

Key Points:
- KONNI leverages generative AI to produce custom PowerShell scripts.
- Campaign targets software developers via phishing lures.
- Backdoors can exfiltrate source code and credentials.
- Attribution links the activity to a North Korea‑aligned threat actor.
Description:
Check Point Research uncovered a new malicious campaign where the threat actor known as KONNI uses AI tools to automatically craft PowerShell backdoor payloads. These scripts are delivered through spear‑phishing emails aimed at developers, enabling remote code execution and data theft once the payload is run.
Why It Matters:
The use of AI to automate malware creation lowers the entry barrier for sophisticated attacks, expanding the threat landscape and forcing defenders to adopt AI‑aware detection methods to identify novel, automatically generated code.
🔵 3️⃣ CISA alerts on publicly available tools in cyber incidents
Key Points:
- Widely shared hacking tools are being employed across health, finance, government, and defense sectors.
- Both state actors and criminal groups take advantage of these freely available resources.
- The tools complicate attribution and defensive planning.
- CISA recommends enhanced monitoring and threat‑ hunting for known tool signatures.
Description:
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) published an advisory highlighting the increasing use of publicly available penetration testing and exploitation tools in real‑world cyber incidents, noting their impact on a broad set of critical infrastructures.
Why It Matters:
The democratization of powerful offensive tools erodes traditional defensive assumptions, making it essential for organizations to update detection capabilities and share threat intel on tool usage patterns.
🟣 4️⃣ GreyNoise CVE Disclosure Early Warning spikes
Key Points:
- Significant rise in traffic to IPs linked with newly disclosed CVEs.
- Early warning alerts help prioritize patching efforts.
- Data shows correlation between traffic spikes and exploit kit activity.
- Provides actionable insight for vulnerability management teams.
Description:
GreyNoise’s platform identified multiple spikes in inbound traffic to IP addresses associated with freshly disclosed CVEs, indicating active exploitation attempts shortly after public disclosure. The service now issues early warnings to subscribers to accelerate remediation.
Why It Matters:
Timely awareness of active exploitation enables organizations to prioritize patch deployment, reducing the window of exposure and limiting potential breach impact.
🟤 5️⃣ Check Point: “The Next WannaCry” vulnerability analysis
Key Points:
- New ransomware‑enabling flaw discovered in widely used Windows component.
- Exploit chain resembles the 2017 WannaCry attack vector.
- Proof‑of‑concept shows rapid lateral movement across networks.
- Patch released; emergency guidance provided for mitigation.
Description:
Check Point Research published a technical brief on a newly identified vulnerability that could serve as the foundation for a ransomware outbreak comparable to WannaCry. The report details the vulnerability’s mechanics, impact, and recommended mitigation steps.
Why It Matters:
Understanding and patching this critical flaw is vital to prevent a large‑scale ransomware campaign that could disrupt essential services worldwide.
🟡 6️⃣ Check Point launches AI‑driven Threat Intelligence enhancements
Key Points:
- Integrates large language models to parse threat feeds faster.
- Automates correlation of indicators across multiple sources.
- Improves detection of AI‑generated malware and phishing.
- Provides contextual scores for urgency and credibility.
Description:
Check Point announced a suite of AI‑powered improvements to its Threat Intelligence platform, leveraging advanced language models to analyze vast amounts of threat data, identify patterns, and flag AI‑augmented malicious activities with higher precision.
Why It Matters:
As adversaries increasingly adopt AI in their attack pipelines, defenders need comparable AI capabilities to maintain situational awareness and respond swiftly to emerging threats.
Stay vigilant and keep your defenses updated.