AI‑driven malware and collaborative threat intelligence dominate 2026 headlines. USB‑based data risks and Zero‑Trust AI advances add urgency 🌐🤖

Hello! Here is your Jan 25, 2026 daily cybersecurity & AI threat intelligence roundup.
Today's headlines
- CTA celebrates 9 years of shared threat intel, highlighting industry collaboration.
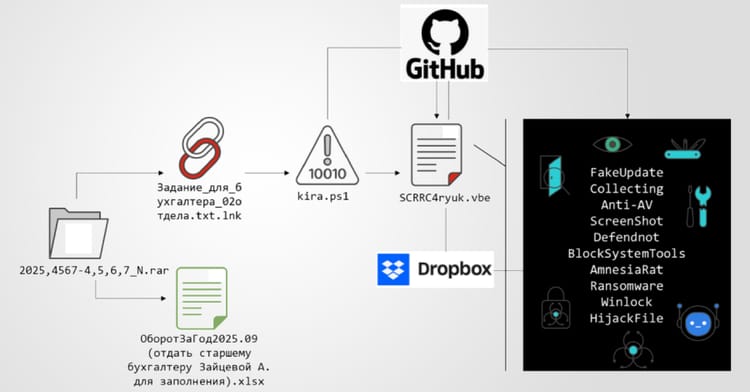
- North Korean‑aligned threat actor KONNI leverages generative AI to create PowerShell backdoors.
- AI simplifies deployment of Zero Trust frameworks, boosting enterprise security posture.
- Removable USB drives emerge as covert vectors for data exfiltration and malware spread.
- Check Point flags a surge in AI‑generated phishing campaigns targeting developers.
1️⃣ CTA Marks 9 Years of Shared Threat Intelligence

Key Points:
- Celebrates nine years of the Cyber Threat Alliance (CTA).
- Highlights collaborative threat data sharing among competing vendors.
- Demonstrates measurable reductions in incident response times.
- Encourages continued member engagement and expansion.
Description:
The Cyber Threat Alliance (CTA) commemorated its ninth anniversary, reflecting on how collective intelligence sharing has become a cornerstone of modern cyber defense. Since its inception in 2014, the alliance has grown to include dozens of leading security firms, enabling rapid exchange of indicators of compromise and tactical mitigations across the industry.
Why It Matters:
Shared threat intel reduces duplication of effort, speeds up detection, and improves overall ecosystem resilience. As threat actors become more sophisticated, coordinated defense mechanisms like the CTA are essential for protecting organizations globally.
2️⃣ KONNI Uses Generative AI to Craft PowerShell Backdoors

Key Points:
- KONNI, a North Korea‑aligned group, employs AI to generate PowerShell backdoor scripts.
- The campaign targets software developers through malicious repositories.
- AI‑crafted payloads evade traditional signature‑based detections.
- Check Point observed over 30 active phishing sites distributing the malware.
Description:
Check Point researchers uncovered a sophisticated phishing campaign where the threat actor KONNI leverages generative AI models to automatically produce PowerShell backdoor scripts. These scripts are tailored to evade static analysis and are distributed via compromised developer forums and code repositories, aiming to infiltrate build pipelines.
Why It Matters:
The use of AI to automate malware creation marks a shift towards scalable, low‑effort attack development, increasing the volume and diversity of threats. Defenders must adopt AI‑enhanced detection and behavior‑based monitoring to counter such dynamic tactics.
3️⃣ AI Boosts Zero Trust Implementation for Enterprises

Key Points:
- AI automates policy generation based on real‑time user behavior.
- Reduces manual configuration time by up to 70%.
- Improves detection of anomalous access patterns across hybrid clouds.
- Integrates with existing identity providers for seamless enforcement.
Description:
VMware’s security research outlines how artificial intelligence can streamline the rollout of Zero Trust architectures. By continuously learning from user activity, AI engines recommend granular access policies, monitor compliance, and trigger automated remediation when deviations are detected.
Why It Matters:
Implementing Zero Trust is critical for mitigating lateral movement, but complexity often hinders adoption. AI‑driven simplification lowers barriers, enabling more organizations to achieve robust security postures without extensive manual effort.
4️⃣ USB Drives Pose Stealthy Data Exfiltration Risk

Key Points:
- Removable media remains a top vector for insider‑driven data theft.
- Malicious firmware can persist beyond standard endpoint scans.
- Enterprise policies often lack granular control of USB usage.
- CrowdStrike recommends hardware‑based encryption and endpoint isolation.
Description:
CrowdStrike’s latest blog highlights the growing threat of USB drives as covert carriers of malware and exfiltrated data. Attackers embed hidden firmware or malicious payloads that can bypass traditional antivirus solutions, especially in environments with lax peripheral controls.
Why It Matters:
Despite advancements in network security, physical media continues to bypass many defenses, exposing sensitive information. Strengthening USB governance is essential for comprehensive data protection strategies.
5️⃣ Check Point Flags Rise in AI‑Generated Phishing Campaigns
Key Points:
- AI tools generate persuasive phishing emails at scale.
- Dynamic content evades language‑based filters.
- Targeted at developers and IT staff to harvest credentials.
- Early detection relies on anomaly scoring and sandbox analysis.
Description:
Building on its investigation of the KONNI actor, Check Point observed a broader trend of AI‑assisted phishing campaigns. These use large language models to craft context‑aware messages, making them harder for users and filters to recognize as malicious.
Why It Matters:
The automation of phishing content increases attack volume and success rates, pressuring organizations to upgrade email security with AI‑powered detection and user awareness training.
6️⃣ Unit 42 Reflects on Collaboration Benefits in Cyber Defense
Key Points:
- Collaboration accelerates threat identification and response.
- Shared indicators create a unified view of emerging threats.
- Member contributions have led to rapid mitigation of major campaigns.
- Future roadmap emphasizes AI‑enhanced data sharing platforms.
Description:
Palo Alto Networks’ Unit 42 recapped the achievements of the Cyber Threat Alliance, emphasizing how joint efforts have enabled faster detection of ransomware, supply‑chain attacks, and novel malware families. The piece outlines lessons learned and upcoming initiatives to integrate AI into the alliance’s data exchange mechanisms.
Why It Matters:
Coordinated intelligence sharing not only improves individual organization security but also raises the collective baseline of defense across the industry, making it harder for adversaries to succeed.
Stay vigilant and keep your defenses up to date.